During the first year of our district’s 1:1 initiative back in 2014, we saw a good example of how persistent students can be when we found that a kiddo had removed a hard drive from their device, connected to their own computer, and used L0phtCrack to crack the local administrator password on the device. Since we were manually managing our devices, all of the local administrator passwords has been set by hand, and they were identical on all 3500 devices. The combination of reusing the password and having a simple enough password that could be hand-entered en masse was a double-whammy, and also incredibly hard to remediate with all of the deployed devices.
In the years since, we’ve lived and learned. With on-prem AD, Microsoft LAPS - short for Local Administrator Password Solution - was a solution for using Active Directory to automatically set unique local administrator passwords on devices, but in our transition to Azure AD, we’ve looked at third party solutions like Cloud LAPS, but starting with the Windows update released on Patch Tuesday last month, Windows is including LAPS as a built-in part of Windows. With LAPS built-in, setting it up for Azure AD is a snap in Intune.
Setting up Windows LAPS with Intune
Sign in to the Intune Admin Center (intune.cmd.ms) and navigate to Endpoint Security —> Account Protection —> Create Policy. On the Create a profile blade, choose Windows 10 and later for the Platform, and under Account Protection choose Local admin password solution (Windows LAPS) and click Create.
Give the Profile a name and description and click Next
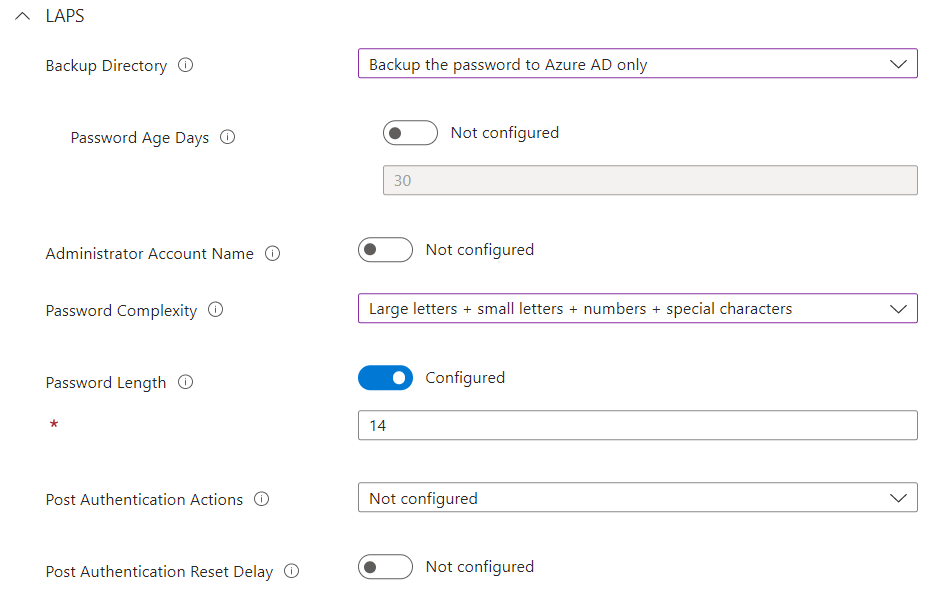
Under Configuration Settings, select the configuration that makes the most sense for your environment. For an AAD/Intune environment, backing up the password to Azure AD makes the most sense. This Backup Directory refers to where the password will actually be managed and can be viewed from. The default for password rotation is 30 days, which is fine for me. For password complexity, I reference the Hive Systems Password table
Select a scope if appropriate
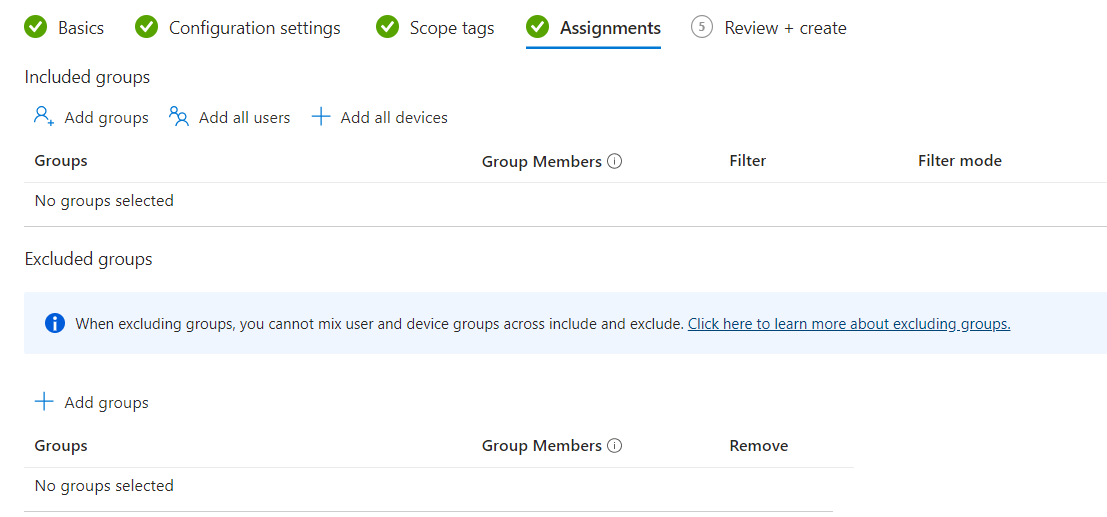
On the assignments tab, apply the LAPS policy to the group you want to manage local administrator passwords for. While there isn’t much that can go wrong that would need to be remediated, it’s always a good idea to test with a sample user or group first. After I was confident that everything worked as expected, I revised the policy to push to all devices. As LAPS is tied to the local administrator account for the machine, I definitely recommend using Device Groups as opposed to User Groups.
Since the appropriate Windows update for LAPS was just released, the policy has only been successfully applying as devices pull the correct Windows update.
Review and create policy.
Checking a Device’s Local Admin Password in LAPS
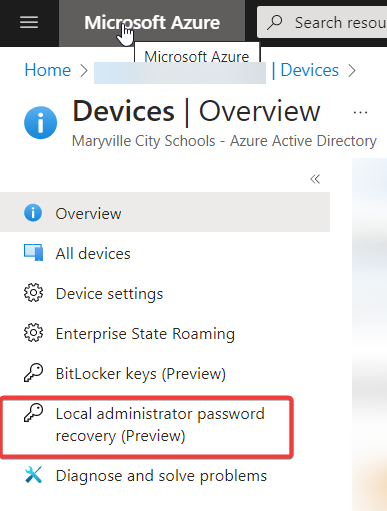
Now that the Intune policy has pushed and the magic has happened, you can check a device’s local administrator password from Azure AD. From the AAD Manage —> Devices tab, select Local Administrator Password Recovery
From the Local Administrator Password Recovery screen, you can search for device.
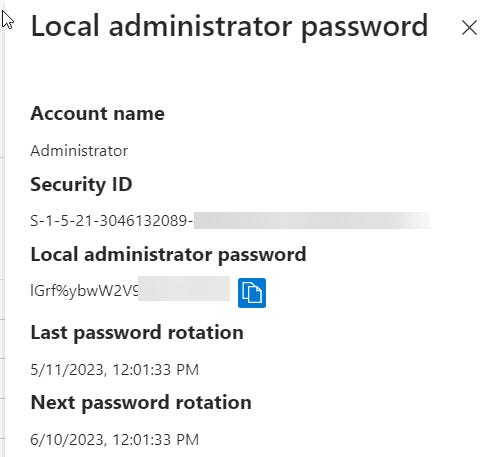
Clicking the “Show local administrator password” link will bring up a blade like below where you can view the local admin password in clear text. You can also see when that password was set, and when its set for rotation.