The first time I tried to set up a hardware authentication token in my M365 environment, I had trouble finding super-clear how-to instructions. Everything I found was either heavily influenced by marketing or leaned hard into the abstract side of setting up MFA. This article is an attempt at making the process clear and simple from purchasing a key to first sign in.
Enabling FIDO2 Security Keys as an Authentication Method
Purchase a FIDO2 hardware token. Yubikey is the brand I’m most familiar with, but as I was wanting to set up a variety of test scenarios and needed a bulk of keys available, I’ve been using the less expensive Identiv uTrust FIDO2 NFC USB key. I was able to purchase these on Amazon for slightly less than $15 compared to the comparably featured Yubikey for $25.
To allow the FIDO2 security key for M365 authentication, go to the Authentication Methods blade in Azure and select FIDO2 security key. (
https://portal.azure.com/#view/Microsoft_AAD_IAM/AuthenticationMethodsMenuBlade)
Select a scope of users to target the availability of FIDO2 security keys. This may vary depending on your environment. On a basic level, configuring this is just making the keys available as an option. If you have other configurations set elsewhere in Azure to require the most secure form of MFA by default, or requiring administrators to use Phish-Resistant MFA, there could be additional impacts. If you have a group you target for policy exclusions, scope it under the Exclude tab. For my sake in this test tenant, I’m applying to all users.
On the configure tab, there are a few options to consider. First, “Allow self-service set up” must be toggled to yes to allow users to enroll their security key. This setting is on by default. The “Enforce Attestation” option is set to No by default. Turning it on requires the security key to pass additional validation testing from Microsoft. Finally, under “Key Restriction Policy” there are two options related to restricting the specific types of security keys that will be allowed. For just starting out with security keys, it’s not something you need to enforce and can stay with the default NO selected. Remember to save the changes you’ve made to the configuration.
Now that security keys are configured and enabled as an authentication method, users can enroll a security key.
Adding a Security Key to Your User Account
Log in to your Microsoft account and go to the account info page at myaccount.microsoft.com and go to Security Info → Update Info
Click on “Add Sign in Method”
Select “Security Key” from the drop down and click on the Add button. If prompted to complete MFA, do so as instructed.
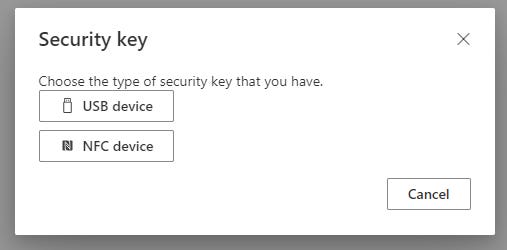
Next, you’ll be prompted to choose a security key type — USB or NFC. If you have a key that can be used for either, it doesn’t matter which you choose. The selection here only refers to which way you want to use for the initial set up — after set up, you can use it as USB or NFC interchangeably.
5. After making a selection, you’ll be prompted to walk through a series of steps to add your key.
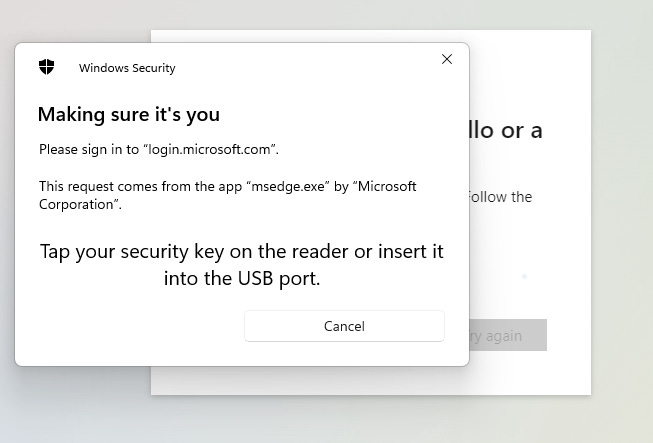
6. When prompted, place your key on the NFC reader or plug it into USB.
You will be prompted to create a PIN. If you’re setting up via USB instead of NFC, you’ll also be prompted to touch the circle in the middle of the key. While a PIN may not feel as secure as a password, the real strength is related to the fact that you have to have physical access to the key (something you have) as well as knowledge of the PIN (something you know) in order for authentication to work. Even if someone knew your PIN, they couldn’t log in unless they had access to the physical USB key. It goes without saying then that you should keep your key secure.
Next, you’ll be prompted to name the key for easy identification in your M365 account information.
And now you’re all set:
And your Microsoft Account info should now show the Security Key listed under sign-in methods.
Signing In with Your New Key
The next time you attempt to sign in to your Microsoft 365 account, there should be an option to sign in with a security key.
2. When you select that option, you’ll be prompted to use your key for authentication like below:
3. You’ll also be prompted for your PIN
And that’s it! You’re now signed in with your freshly configured security key!
Resources:
Passwordless security key sign-in - Microsoft Entra ID | Microsoft Learn