We began in Part 1 talking about spoofing and how SPF can help prevent impersonation. In Part 2, we talked about how DMARC couples with SPF to help further protect your mail from spoofing. Part 3 will pull DKIM into the mix. This article was originally included in Part 2, but as the word count kept inching up, I decided to pull it out and stash it here for reference.
Editing Headers in Telnet
One way you can have success testing out spoofing is using telnet and 10minutemail.net. This site serves up disposable email addresses that expire after 10 minutes. That gives us a place to test sending messages.
The address I got is efm47528@nowni.com. To start spoofing, we need to find out what the mail server is for this domain. You can use a tool like MX Toolbox, or you can dig it from Linux or Mac using this command:
dig mx nowni.com 25 +short
This will output the mailserver. In this case, mail.nowni.com.
Next, there’s a series of commands we can do to send an email message over telnet. If you’re not familiar with telnet, it’s an insecure protocol that was later replaced by SSH (so don’t send anything over it that you don’t want others to see). As such, it’s disabled by default, so if you’re following along you’ll need to enable it in Windows. If you’re working Linux, you’ll possibly need to install it (apt install telnet).
In our terminal, complete each line then hit enter. At the end, you’ll do a line with just a period (.) and then hit enter to send the message. In this example, we’re going to be sending mail as Sam@walmart.com:
telnet mail.nowni.com 25HELO edtechirl.comMAIL FROM: <sam@walmart.com>RCPT TO: <efm47528@nowni.com>DATAContent-Type: multipart/mixed; boundary=”NextMimePart”From: sam@walmart.comTo: efm47528@nowni.comSubject: Howdy!--NextMimePartContent-type: text/html;How’s it going my dude?.In the terminal, it will look like this:
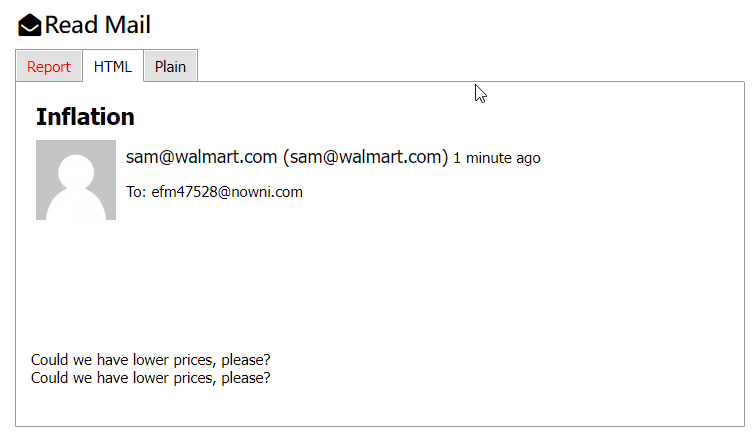
The resultant message in 10minutemail will look like this:
And now we’ve sent our first spoofed email. This lack of sender verification is the first open door for social engineers to begin impersonating you or your users.
Altering Headers in Thunderbird
In addition to sending spoofed messages using telnet, there is also a Thunderbird email client add-on called Header Tools Improved that can also give you an idea of what it looks like when you manipulate headers. However, depending on your email provider, they probably won’t allow you to send messages with a mismatch between your account’s address and the From address. This method is helpful, however, for letting you manipulate headers to see the direct impact it has on a message in your mail client.
Step 1: Install Thunderbird and add the Header Tools Improved add-on to Thunderbird (https://addons.thunderbird.net/en-US/thunderbird/addon/header-tools-improved/)
Step 2: Start a new message in Thunderbird and save it as a draft. This is important, because you can only access the Header Tools add-on from the message pane.
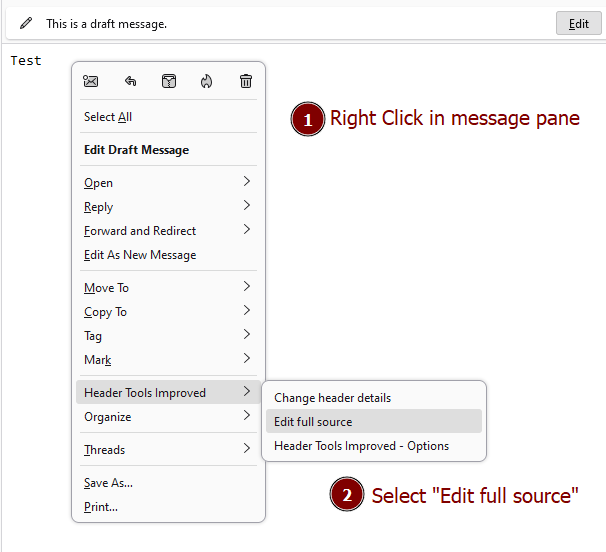
Step 3: Right click in the body of the message and select Header Tools Improved —> Change header details. Go to the Edit full source option.
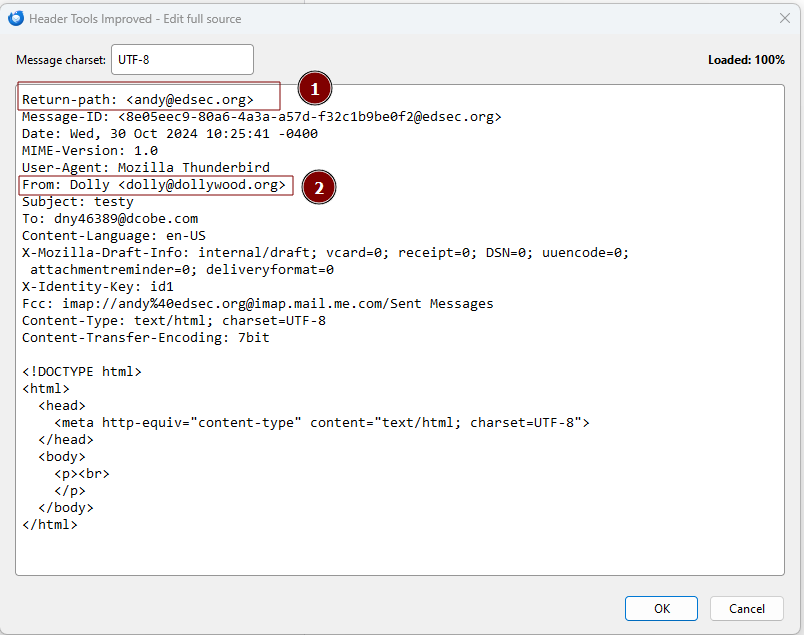
Step 4: Edit the headers you want to change (e.g.,
From,To,Subject). Here, I’m adding the Return-Path header to the beginning of the message. This should be the address that can pass SPF. Then, I’m altering the From header to show the email address I want the recipient to see.
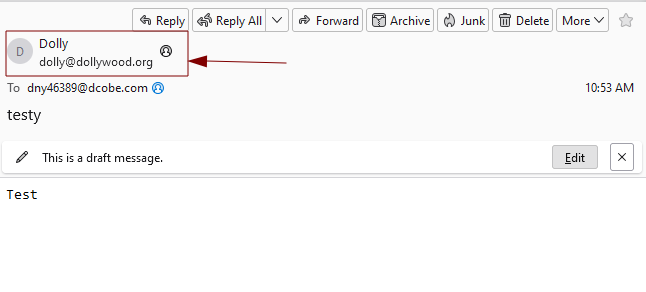
Step 5: Now, the message in Thunderbird should reflect the change in the From header.
At this point, if your email platform doesn’t restrict actions like this, you can hit send and the message will land in someone’s inbox with a pass for SPF showing Dolly as the sender (assuming their domain doesn’t have additional spoofing protections in place).
How Would an Attacker Do It for Real?
Thankfully, this has gotten a little more difficult than it was 10-15 years ago. Thanks to crackdowns in Spam sending, most ISPs and cloud providers don’t allow you to send SMTP traffic without validating a legitimate usage. To get around this, attackers use a variety of methods, ranging from compromising infrastructure to abusing existing tools.
Compromised Email Servers
Attackers often hack into legitimate email servers or steal login credentials for legitimate accounts (or, if they’re lucky, find an SMTP server that’s misconfigured as an Open Relay), then use these accounts to send phishing emails. When attackers send messages this way, the messages are coming from legitimate domains and are more likely to bypass spam filters, especially if they have good email reputations or authenticated SPF, DKIM, and DMARC records. This is a common problem for small and medium-sized businesses, especially those with weaker security on their email systems.
Botnets
Botnets are networks of infected devices controlled remotely. Attackers can leverage thousands of compromised devices to send out large volumes of phishing emails, making it difficult to trace the source. This is effective because botnets distribute the email-sending load across many devices with various IPs, reducing the likelihood of detection by email providers.
Bulk Emailing Services Used Illicitly
Attackers sometimes gain access to popular bulk emailing platforms, like SendGrid or Mailgun, through stolen API keys or compromised accounts. These platforms have high deliverability rates and built-in infrastructure, making it easier for attackers to reach targets. On the positive side, this misuse is typically short-lived, as the platforms will block the account as soon as suspicious activity is detected.
Bulletproof Hosting Providers
These providers offer hosting and SMTP services that are lenient about or ignore reports of abuse. They provide servers that allow attackers to send phishing emails without as many restrictions. Bulletproof hosting is often offered in regions where laws and enforcement on spam are more lax.
DIY SMTP Servers
Some attackers configure their own SMTP servers on compromised servers or rented cloud servers to send bulk emails. By rotating IP addresses and domains, they can avoid being flagged by spam filters. This provides greater control over the server and allows attackers to manipulate email headers to evade spam filters. This setup can also bypass provider restrictions. Attackers must work harder to ensure emails are not flagged by spam filters, as emails from untrusted SMTPs are more likely to be blocked, but the basic setup for this can be done with nothing more than a Linux laptop running Postfix. As an additional level-up, attackers can misuse defensive tools like the GoPhish framework to manage large phishing campaigns with pre-built templates out of the box.
Phishing-as-a-Service (PhaaS)
The easy button of Phishing, PhaaS kits available on the darknet or through underground networks provide full phishing infrastructure, including email templates, sender services, and evasion techniques. These services make it easy for attackers with minimal technical skills to launch sophisticated phishing campaigns.
Free Email Providers (Abuse)
Attackers may create large numbers of free email accounts on platforms like Gmail, Yahoo, or Outlook and use them to send phishing emails. This method has become less common as providers have improved security and limit bulk emails from new accounts. Emails from well-known domains have high deliverability, and reputable free email providers may initially bypass spam filters.
Cloud Services for Phishing Infrastructure
Attackers sometimes use cloud providers, like Amazon AWS or Google Cloud Platform, to host phishing sites or to run automated email-sending scripts. While the cloud providers detect and block abuse quickly, attackers exploit trial periods or use stolen credit card information. We can thank this for Microsoft’s removal of their free M365 Developer Tenants 🤬. The benefit of this for attackers is that the high IP reputation and built-in scaling make it easier for attackers to reach a broad audience quickly before the infrastructure is shut down.
Conclusion
We've now looked into various methods that attackers use to exploit email systems and manipulate headers to spoof identities—starting with basic spoofing techniques and progressing to more complex, real-world attack strategies. Understanding these techniques is crucial for building stronger defenses against email-based attacks. By being aware of how spoofing and phishing operate, we can better appreciate the role of layered security protocols like SPF (Part 1), DMARC (Part 2), and DKIM (Part 3), as well as the importance of educating users about phishing risks. Continuous vigilance, combined with robust email authentication and proactive monitoring, remains essential for protecting ourselves and our organizations from these increasingly sophisticated threats.